compromise assessment malaysia
To establish trust in the IT environment for the board and executives CyberStash conducts forensic-level analysis across the entire IT fleet at a frequency defined by the organizations. Use of advanced malware by sophisticated attackers is becoming an increasing threat to organisations today as it enables them to remain undetected.

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System
A compromise assessment will provide visibility into whether there is an active compromise or a compromise in the past in that organization Ledzian says in an interview with Information Security.

. Even for large-scale assignments. The goal of a compromise assessment is to hunt down evidence of potential threats by identifying IOCs and backing them up with hard data. We follow a standard 3-step methodology which is both non-invasive and non-disruptive.
Attack Phase TargetingExploiting. Post-Attack Phase Documenting and Reporting. 13 For details of the Banks macroeconomic outlook refer to the BNM Quarterly Bulletin 2Q 2020.
It takes organizations an average of 191 days to identify a data breach. The CrowdStrike Compromise Assessment is designed to identify ongoing or past attacker activity in an organizations environment. Detect hidden adversaries in your IT environment.
Understanding when we are breached and resolving it should be the top priority. Compromise assessments CA answer the fundamental cyber security question Are we breached. These advanced malware can potentially lead to reputational damage data loss theft regulatory fines and operational disruption.
Bank Negara Malaysia now encourages financial institutions to conduct a Compromise Assessment CA through a qualified professional service provider. To seek the evidence of possible risks a Compromise Assessment will be running on detecting indicators of compromise IoC and correlating them with hard data. An Ad-Hoc Compromise Assessment is performed when there is a specific IR case or the customer requests an assessment of the system landscape for the purpose of a merger or general review.
Engender a more proactive approach to cybersecurity. Of Stress Testing in Malaysia in the BNM Financial Stability and Payment Systems Report 2012. For example network applications may use more bandwidth than usual to send and receive traffic maybe to an obfuscated unsecured site.
Pre-attack Phase Research Information Gathering Phase 2. Assessments are based on independent reviews of your organizational infrastructure systems and applications to detect backdoors OS manipulations. It is a snapshot that provides clarity on the situation within the system landscape from the time of the scan sometimes going back to the installation date of the system.
Your essential post-breach strategy for detecting systems already compromised by attacks that are too sophisticated for your existing security controls to catch. Steps of a Compromise Assessment Step 1. Compromise assessment teams can use the collected data to determine has there been an attack.
Compromise Assessment Compromise assessments can detect known and unknown zero-day malware and persistent threats that have evaded your security defenses and may be active or dormant in your network. Usually there are a few reasons companies do a Compromise Assessment. Most Compromise Assessment engagements will last.
Contact us for a free quotation today. Detect and respond to security threats and risks proactively. 14 Used by banks to inform the setting of internal capital targets as part of the Internal Capital Adequacy Assessment Process ICAAP.
A Compromise Assessment CA is a comprehensive automated evidence-based analysis and evaluation of an organizations entire digital environment and cybersecurity posture and is designed to. It leverages the Services teams decades of experience in responding to intrusions by the most advanced attackers the powerful CrowdStrike Falcon platform industry-leading cyber threat intelligence and 247 threat hunting to deliver the most. Bank Negara of Malaysias Risk Management in Technology.
A compromise assessment begins with a collection of forensic data searching for signs of potential compromise in endpoints network traffic and logs. KPMGs compromise assessment is a tailored objective technical review of your organizations network to find instances of compromise backdoors unauthorized access and anomalous activity. 2 To identify the presence of any security breaches.
Research has shown attacks that have prolonged access. The methodology used by cyber adversaries. Key loggers or credential-stealing malware may.
1 To comply with local laws regulations Eg. Our CA service delivers a high-level review and audit of your organizations IT environment based on suspicious user behaviors logs compliances policies Indicators of Compromise IOCs or any evidence of malicious activities. Although different cybersecurity services follow different methods to conduct a penetration test all of them more or less come down to the same three phases.
For example network applications might be using more bandwidth than normal to send and receive traffic and may be sending it to an obfuscated insecure server.

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System

Experian Malaysia Gets Bnm Nod To Resume Ccris Access Digital News Asia

Experian Malaysia Gets Bnm Nod To Resume Ccris Access Digital News Asia
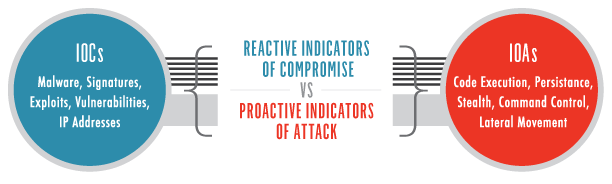
Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

Proactively Hunt For Threats With Managed Xdr Group Ib

James Hung Senior Director Of Incident Response Engineering Cybereason Linkedin

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System
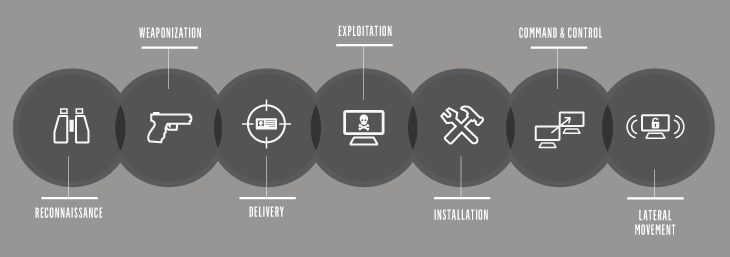
Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

Cloud Security Services Crowdstrike Services
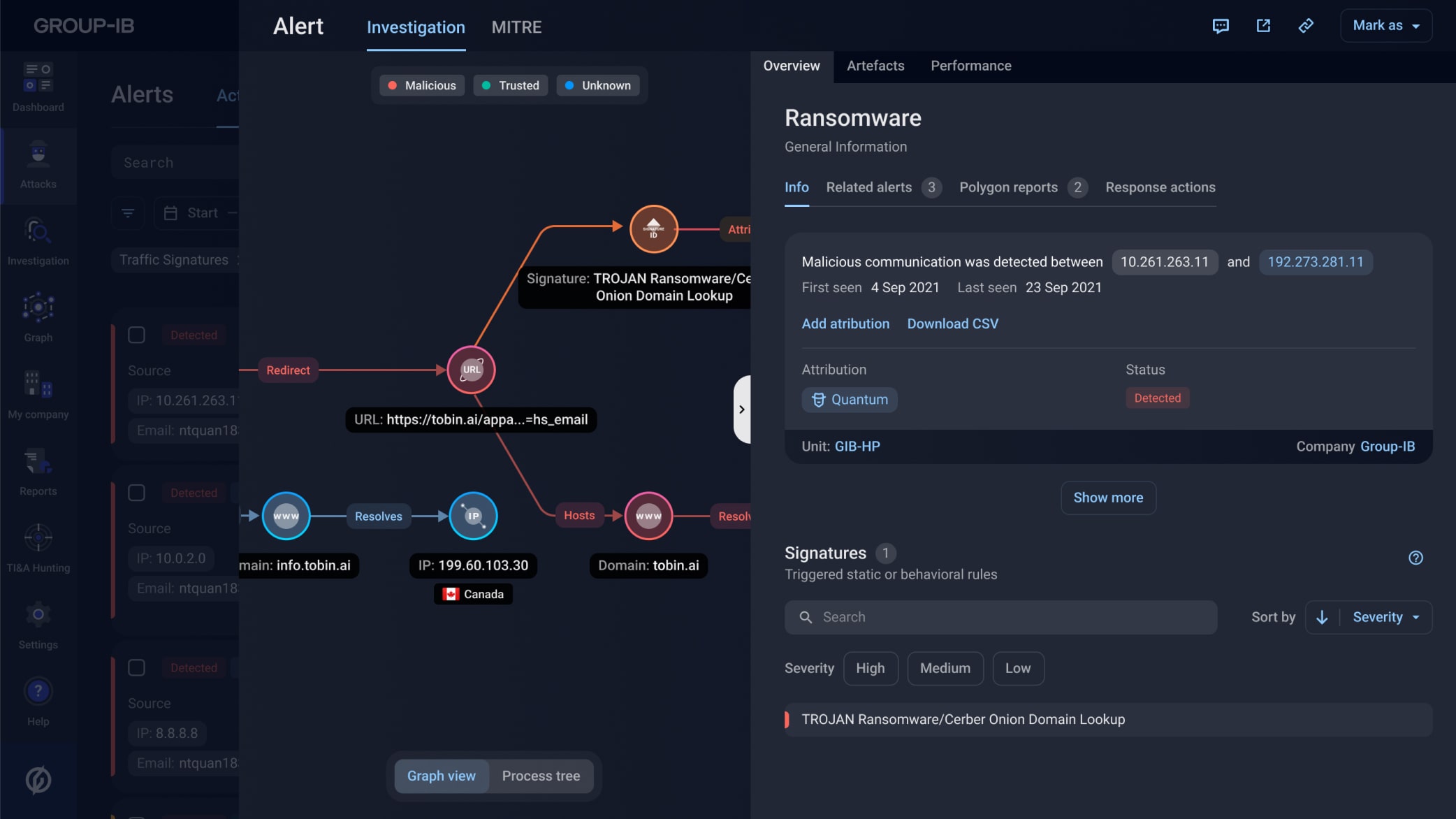
Proactively Hunt For Threats With Managed Xdr Group Ib
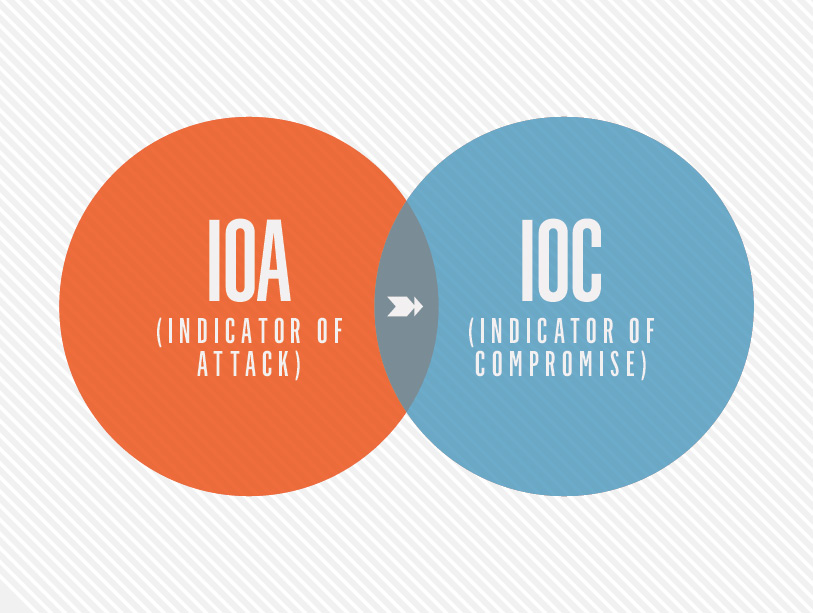
Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

Fireeye With Kddi Kddi Philippines

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System





Comments
Post a Comment